My Close Call with a Carousell Smishing Scam This Christmas

Not even your friendly neighborhood cybersecurity analyst is immune to phishing and e-commerce scams. This Christmas season while using popular e-commerce and P2P selling platform Carousell I encountered a malicious fraud campaign targeting Hong Kong and Asia shoppers.
The Encounter
Christmas is the time of year people all around the world engage in e-commerce activity. We buy gifts for friends and loved ones or sell whatever we feel we might have outgrown. It all started when I listed an item for sale on Carousell. A potential buyer quickly showed interest, claiming they were disabled and wanted to purchase the item as a gift for their daughter. They seemed genuine and even offered their WhatsApp number, asking me to send pictures of the product.
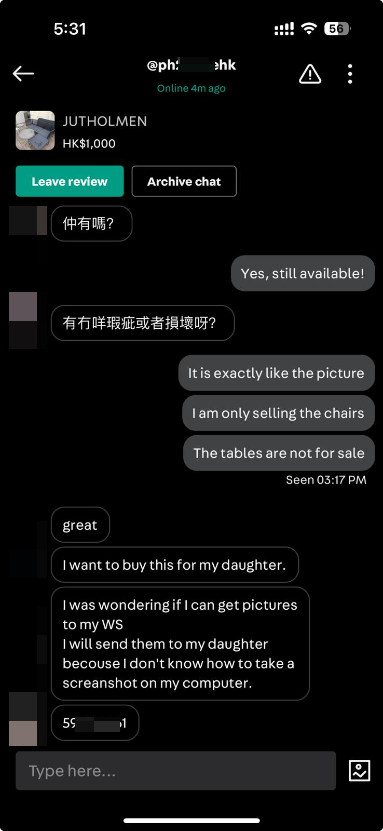
At first, everything seemed normal. I sent the requested images, thinking it was just another routine transaction...
The Red Flags
However, things took a suspicious turn when the buyer sent me a link via a URL shortener. The link redirected to a domain with an irregular top-level domain: carousell-fps.easyfps.run. This was my first red flag.
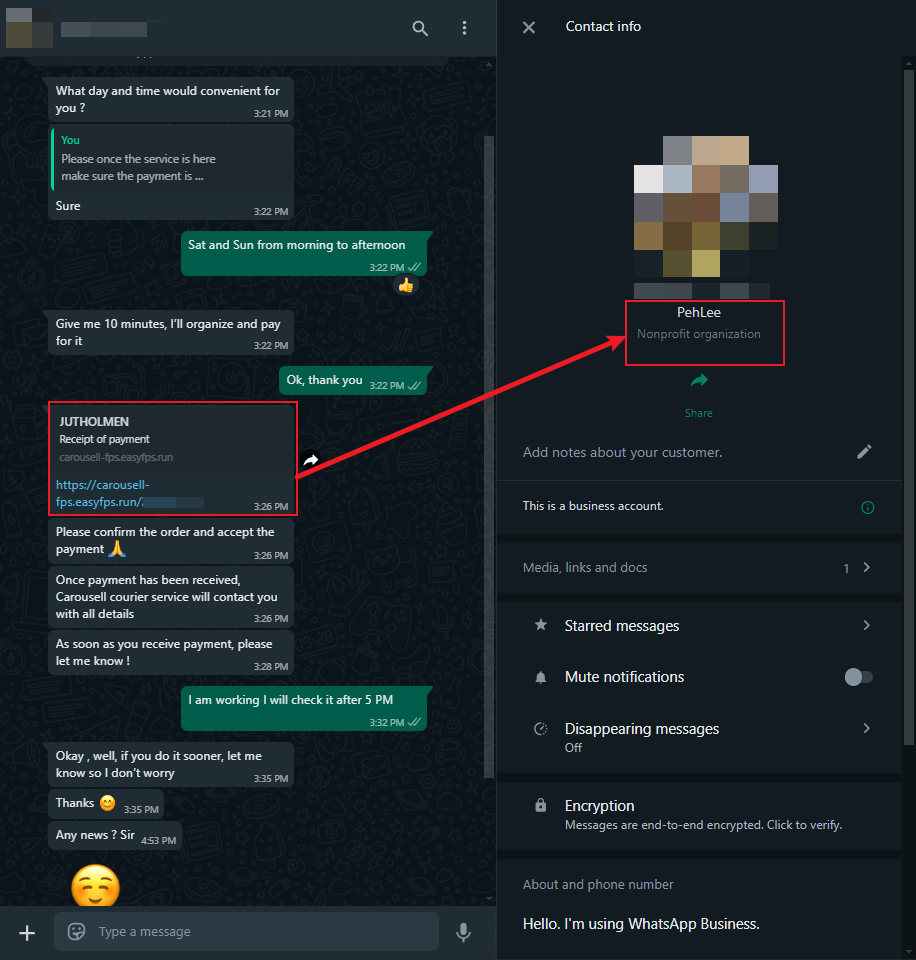
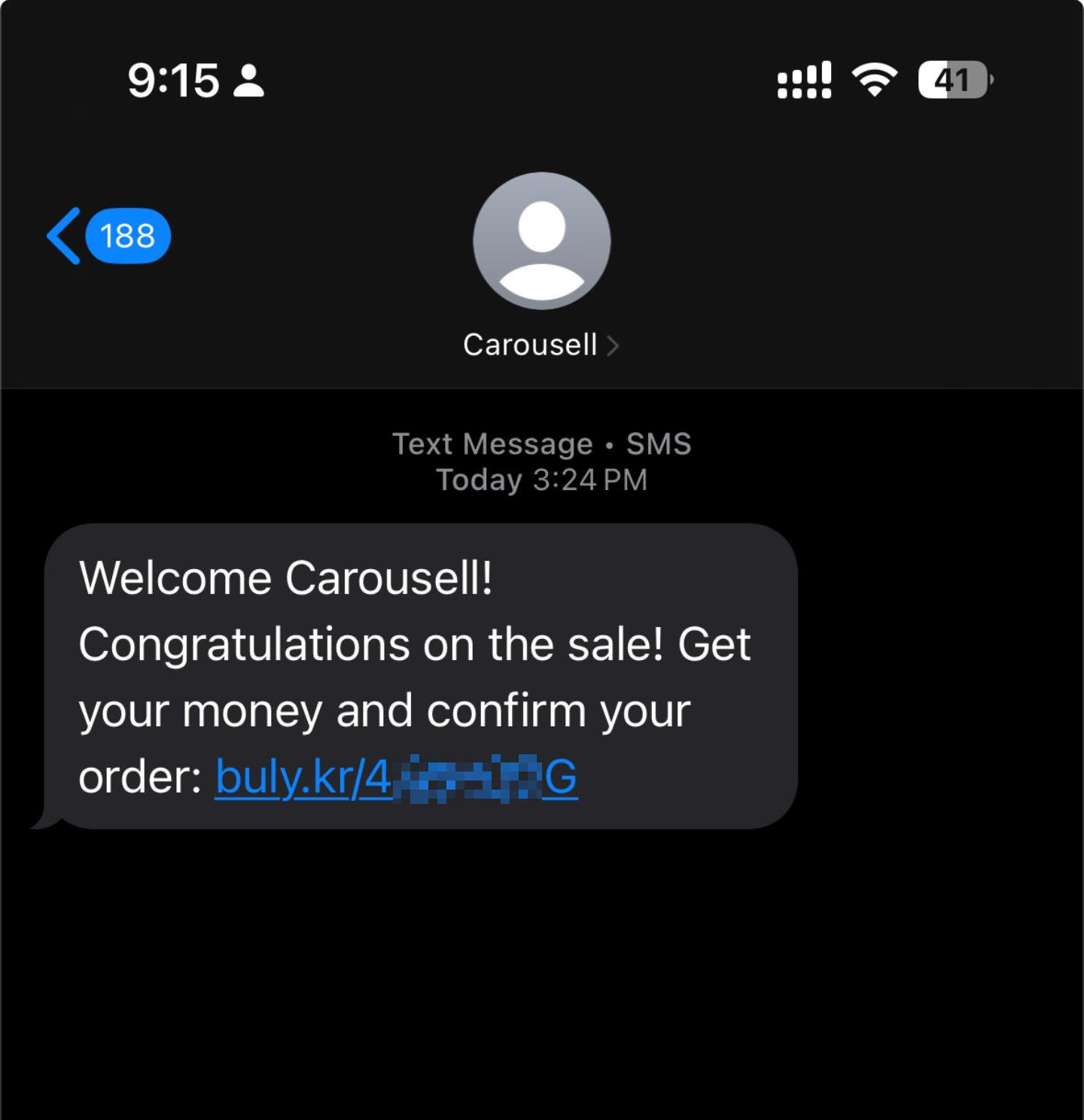

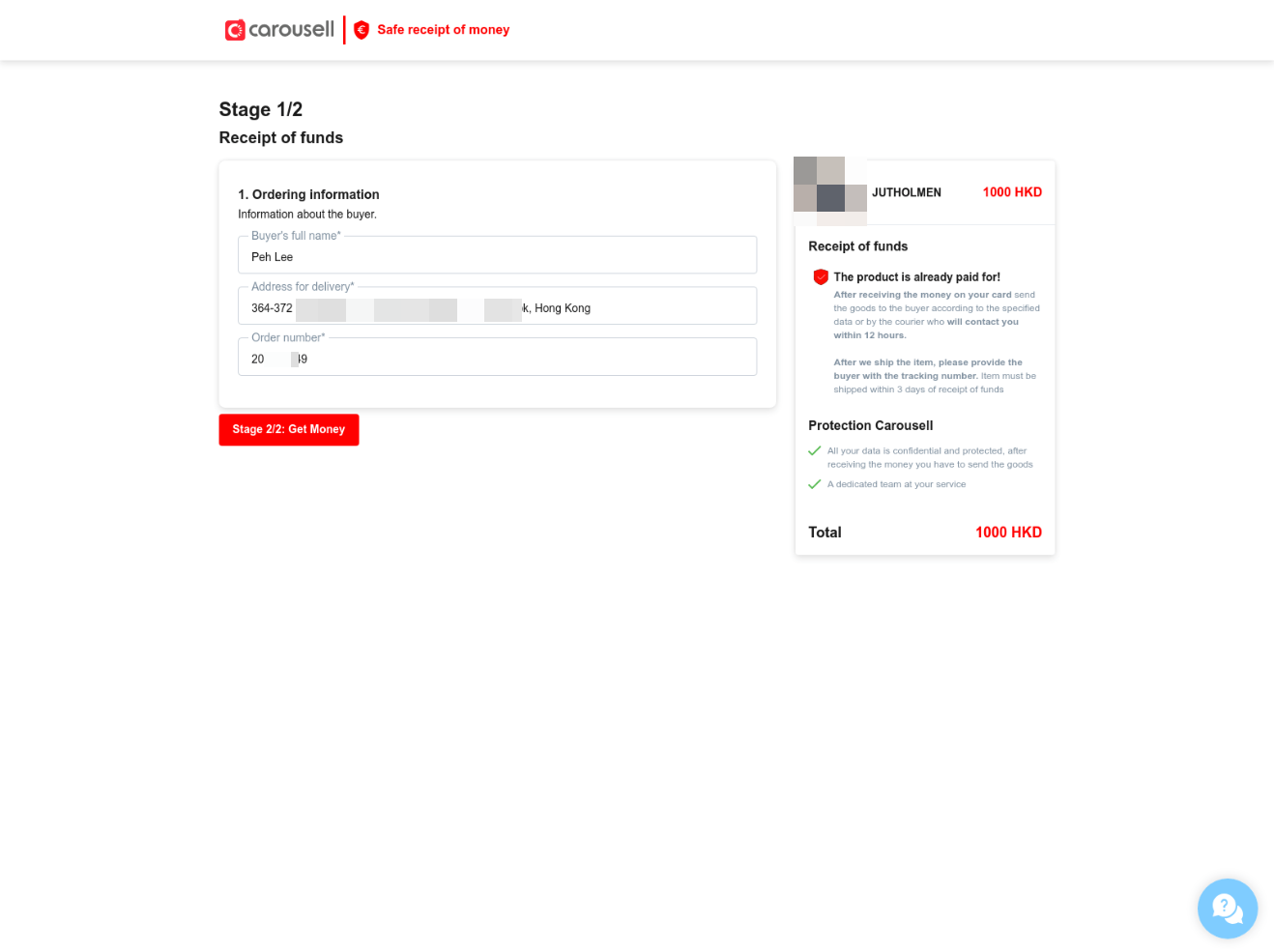
Upon clicking the link, I was taken to a page that displayed my product and the price the buyer claimed they would pay. The page even included a screenshot of my product as well as its listed price along with prefilled name and order number making it seem like a legitimate service.
The Scam Unveiled
The final step was to confirm the transaction, which redirected me to a page listing multiple Hong Kong and Mainland China banking providers.

Here, I was asked to provide my e-banking information. This was the moment I realized something was seriously wrong.
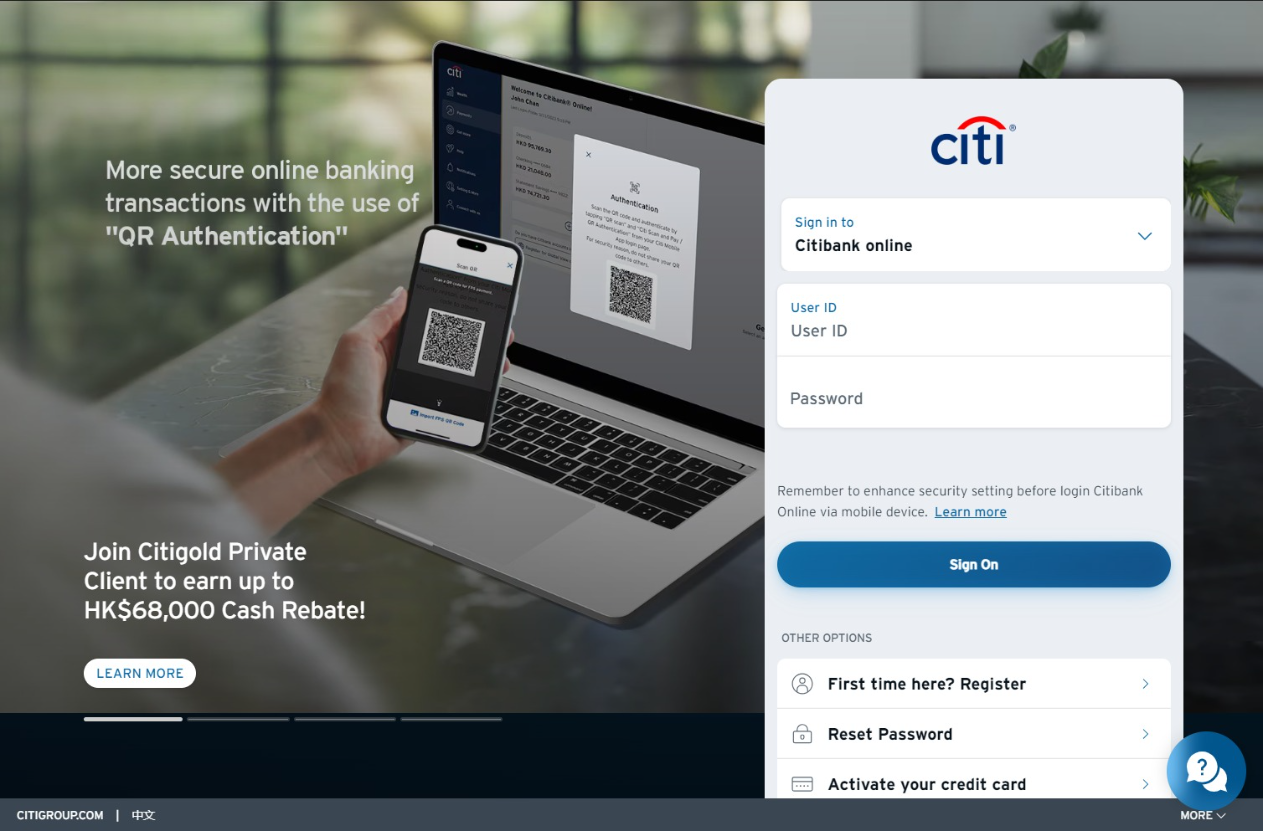
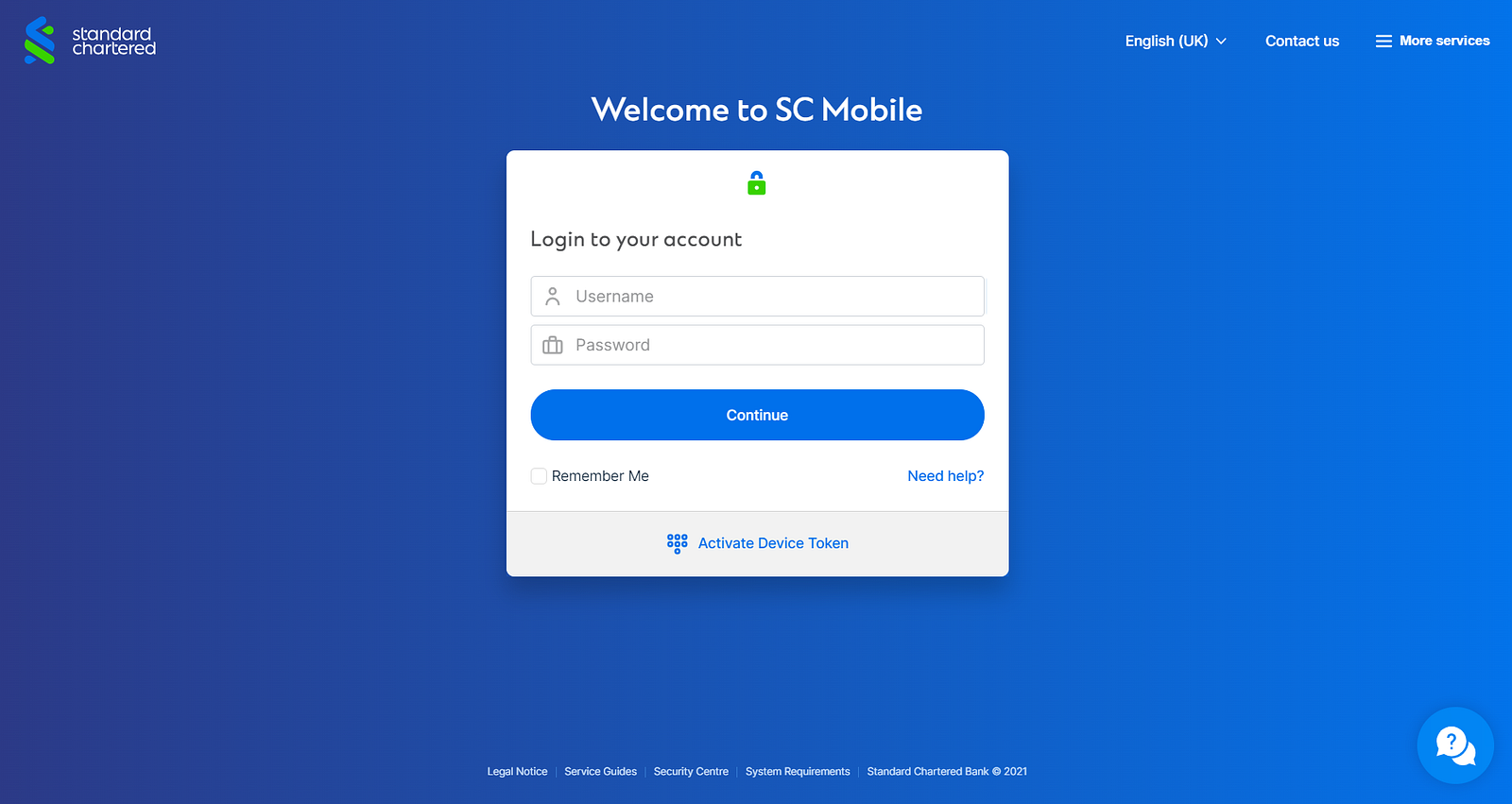
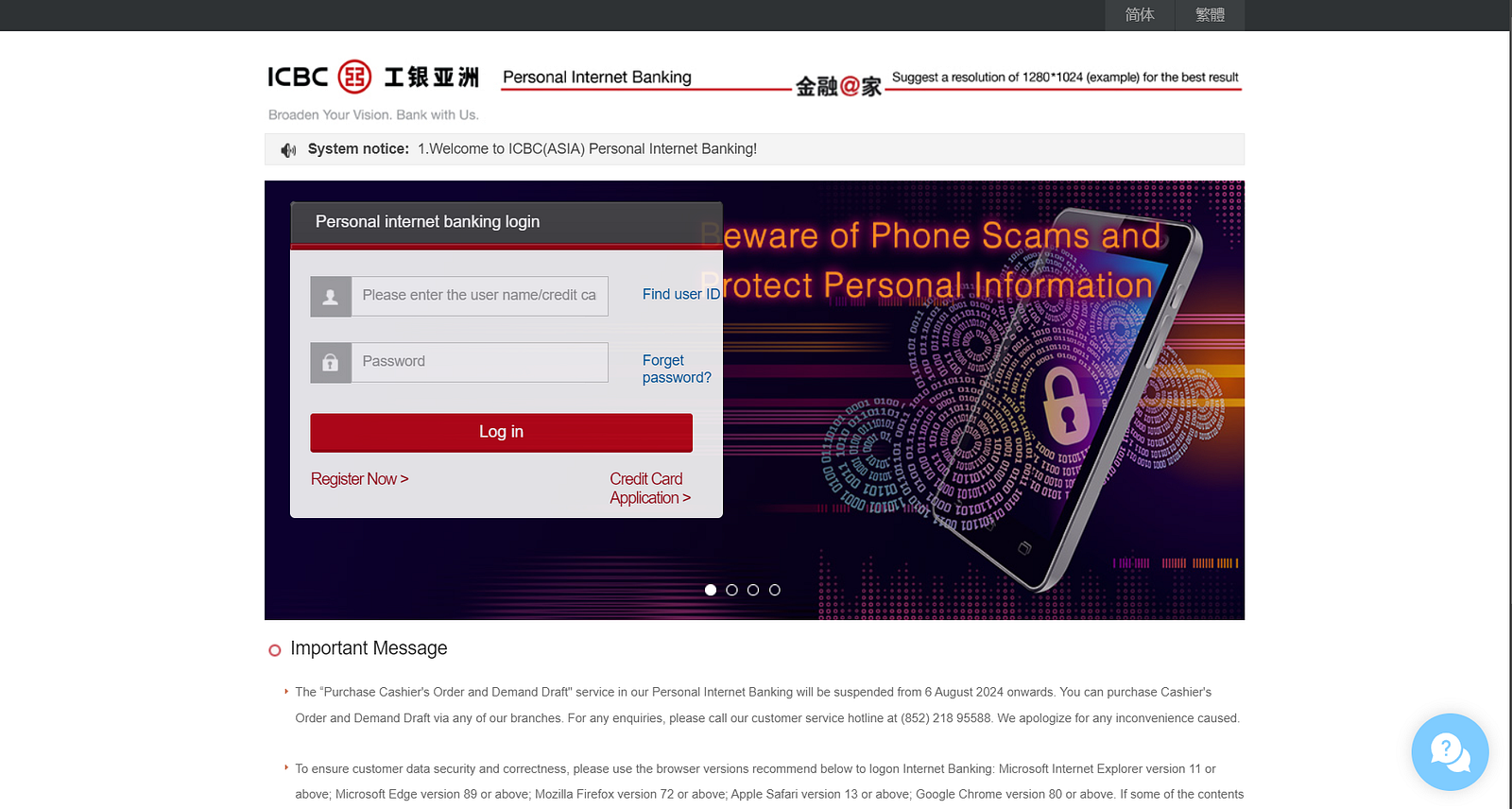

Interacting with these domains showed that none of the buttons were interactive and more importantly they were not redirecting to their respective banking sites. All of the pages were hosted on the malicious domain (carousell-fps.easyfps.run).
To understand the scam better, I entered some dummy information to see where it would lead.
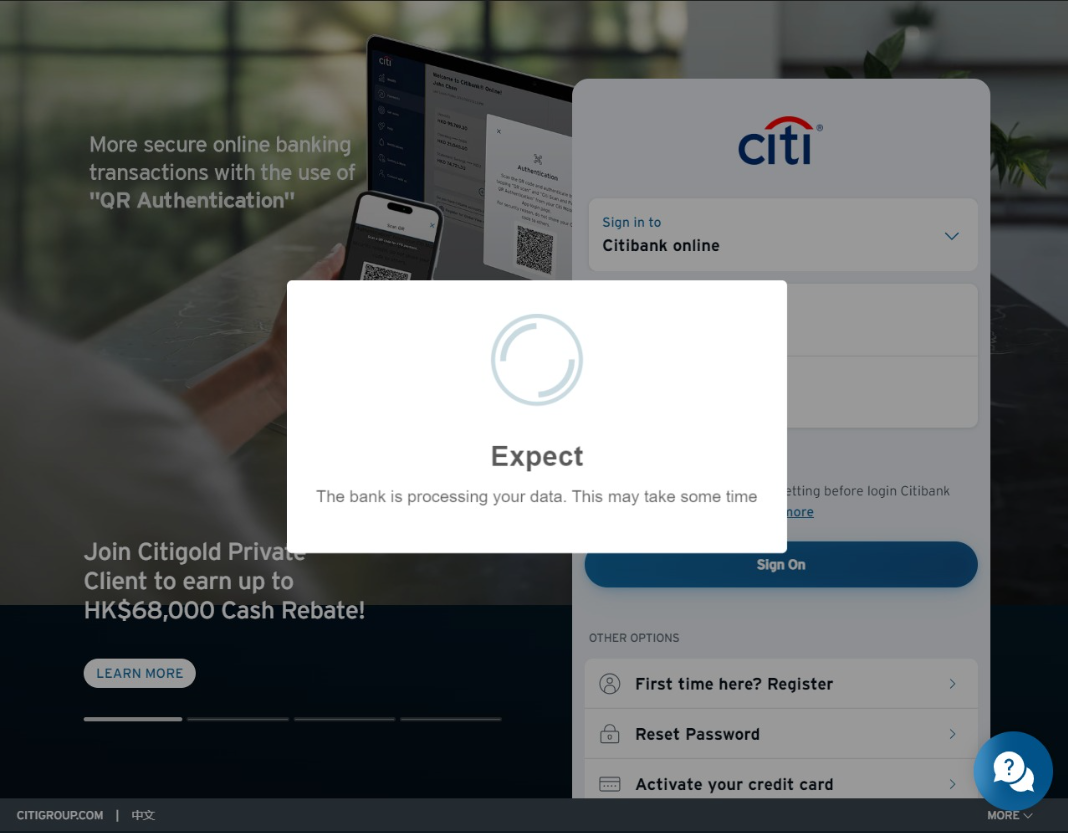
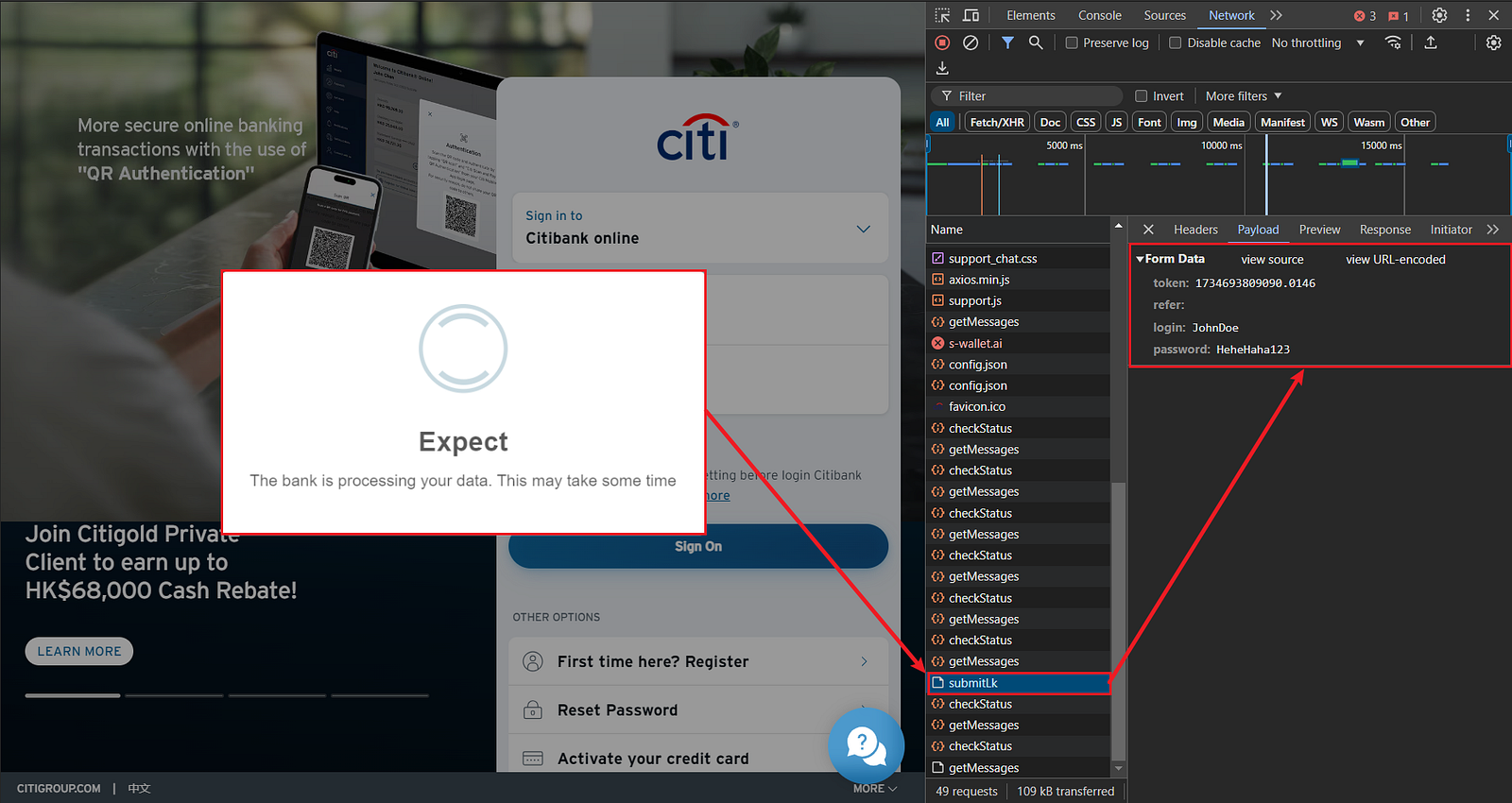
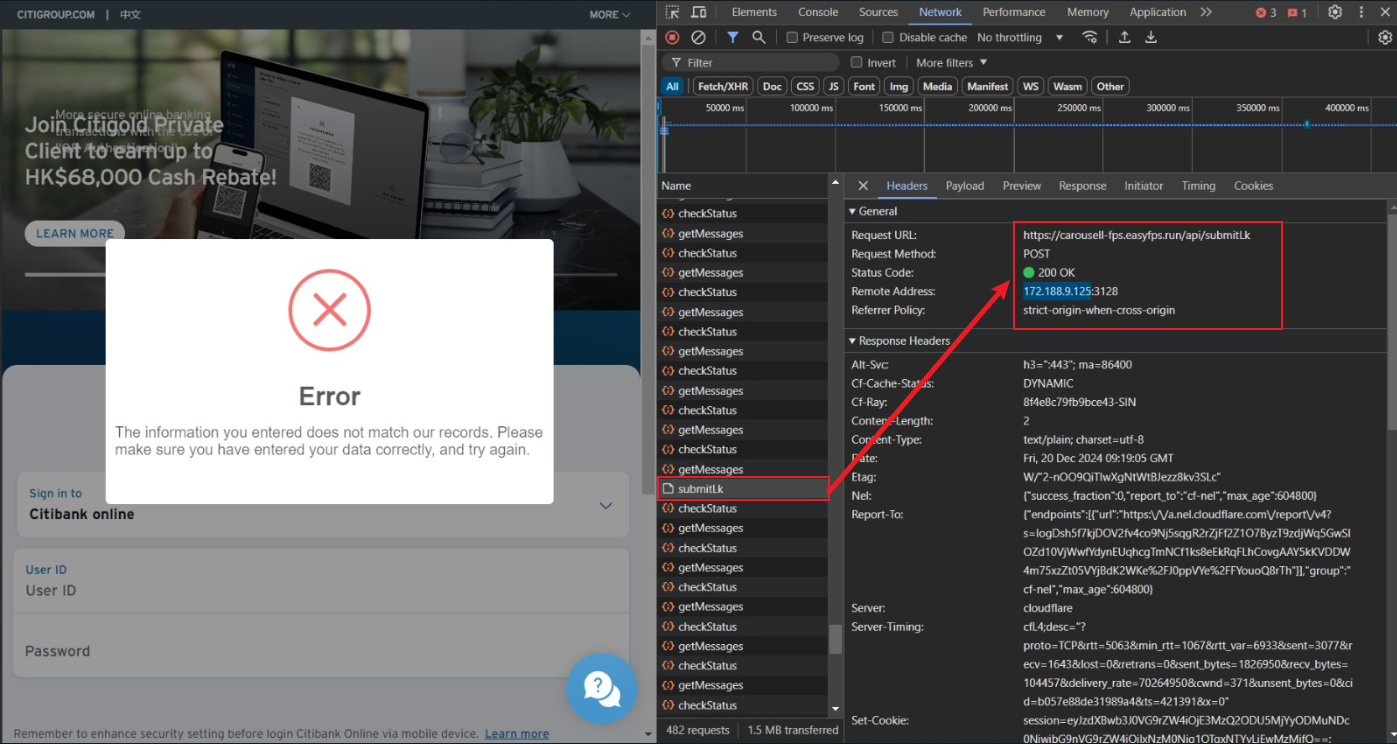
The webpage made a request to:
- Request URL:
https://carousell-fps.easyfps[dot]run/api/submitLk - Request Method: POST
- Status Code: 200 OK
- Remote Address: 172.188.9.125:3128
What Happened
- Request URL: This is the web address where your information was sent. In this case, it’s a part of a phishing scam pretending to be a legitimate service.
- Request Method: POST: This means that data (in this case, the information you entered) was sent to the server. POST requests are commonly used when submitting forms on websites or interacting with Application Programming Interfaces (APIs).
- Status Code: 200 OK: This indicates that the server successfully received and processed the request. In other words, the server got the information you entered without any issues.
- Remote Address: This is the IP address of the server that received your data. It’s like the server’s “home address” on the internet with the specific port 3128 (default port for many proxy applications).
Implications
- Data Capture: The fact that the server responded with “200 OK” means that it successfully captured the information entered. Even though I used dummy data, if it had been real, the scammers would now have access to it.
- Phishing Success: This is a clear indication of how phishing scams work. They create fake websites that look real to trick people into entering sensitive information, like credit card details or e-banking credentials.
The Investigation
Curious about the extent of this scam, I tracked the campaign and discovered it had been active from June 3, 2024, to December 20, 2024. During this period, at least 85 submissions of these fraudulent websites were posted to URL scan alone.
Mapping the Threat Actor’s Reach
As I delved deeper into the data, I noticed an interesting pattern. The geographical distribution of these phishing attempts reveals telling insights into our threat actor’s scope of operation.
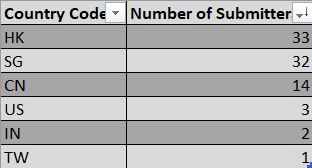
The data paints a clear picture of where this threat actor is most active:
- Hong Kong and Singapore: These two territories stand out as the primary targets, accounting for the majority of submissions.
- Mainland China: Following closely behind, indicating a significant presence in the region.
- Other Countries: Smaller but still notable submissions from various other nations.
This regional footprint likely arises from the threat actor’s strategy of targeting individuals on Carousell, reflecting the platform’s popularity in these areas. This is particularly concerning during the holiday season, a time when online scams are known to surge.
IOC’s, Key Patterns and Tactics
# | Malicious domain
1 | carosell[dot]bankfps[dot]shop
2 | carousel[dot]transwallet[dot]shop
3 | carousell[dot]asiafps[dot]shop
4 | carousell[dot]asia-fps[dot]shop
5 | carousell[dot]asiawallet[dot]shop
6 | carousell[dot]asia-wallet[dot]shop
7 | carousell[dot]bankfps[dot]shop
8 | carousell[dot]bank-hk[dot]shop
9 | carousell[dot]bank-verify[dot]shop
10 | carousell[dot]bank-wallet[dot]shop
11 | carousell[dot]byfps[dot]shop
12 | carousell[dot]choose-fps[dot]shop
13 | carousell[dot]fastfps[dot]world
14 | carousell[dot]fps-asia[dot]shop
15 | carousell[dot]fps-from[dot]shop
16 | carousell[dot]fpsget[dot]shop
17 | carousell[dot]fps-get[dot]shop
18 | carousell[dot]fpsprocessing[dot]shop
19 | carousell[dot]fpsquick[dot]shop
20 | carousell[dot]fps-recieve[dot]shop
21 | carousell[dot]fpssecure[dot]shop
22 | carousell[dot]fpstrade[dot]shop
23 | carousell[dot]fps-wallet[dot]club
24 | carousell[dot]get-fps[dot]shop
25 | carousell[dot]getfps[dot]world
26 | carousell[dot]moment-fps[dot]shop
27 | carousell[dot]payprocessign[dot]shop
28 | carousell[dot]paywithbank[dot]shop
29 | carousell[dot]recievefps[dot]shop
30 | carousell[dot]s-walet[dot]pro
31 | carousell[dot]s-walet[dot]shop
32 | carousell[dot]tradefps[dot]shop
33 | carousell[dot]trade-fps[dot]shop
34 | carousell[dot]trafferwallet[dot]shop
35 | carousell[dot]transfer-verify[dot]shop
36 | carousell[dot]transferwallet[dot]shop
37 | carousell[dot]transfer-wallet[dot]shop
38 | carousell[dot]trans-wallet[dot]shop
39 | carousell-fps[dot]easy-fps[dot]shop
40 | carousellorder[dot]easy-fps[dot]digital
41 | carousellorder[dot]fps-wallet[dot]com
42 | carousellorder[dot]fps-wallet[dot]life
43 | carousellorder[dot]fps-wallet[dot]live
44 | carousellorder[dot]momentfps[dot]digital
45 | carousellorder[dot]momentfps[dot]world
46 | carousellorder[dot]moment-fps[dot]world
47 | carousels[dot]fps-trade[dot]shop
As I delved deeper in my investigation of these scams, the naming conventions of the malicious domains stood out as a critical component of this and other previously encountered campaign strategies. These domains are crafted to mimic legitimate services, thereby luring unsuspecting victims into a false sense of security.
- Use of Target Brand Name(s): The domains predominantly incorporate “carousell,” a well-known e-commerce platform and likely victim platform of choice. This tactic is designed to deceive users into believing they are interacting with Carousell’s site, which is consistent throughout the fraudulent user experience where we see Carousell's brand and logos being used in the initial fraudulent order forms.
- Financial and Transactional Keywords: Words like “bank,” “wallet,” “transfer,” and “pay” are prevalent across these domains.
- Technical Jargon and Abbreviations: The repeated use of “fps” (known to locals and residents of Hong Kong; the popular payment system “Faster Payment System” (FPS)). This is intended to mislead users into thinking they are interacting with a known and familiar service.
- Regional Indicators: Some domains include regional identifiers such as “asia” and “hk,” which may be intended to target users in specific geographic locations, aligning with the observed regional focus of the threat actor.
Lessons Learned
This experience served as a reminder to always remain vigilant when conducting online transactions. Here are a few tips to help others avoid falling victim to similar scams:
Think Before You Click: Never click or tap on links from unknown/ unverified sources. This simple yet powerful practice can be your first line of defense against cyber threats.
Verify URLs: Always check the URL for irregularities or unfamiliar domains.
Protect Personal Information: Never provide sensitive information unless you’re certain of the recipient’s legitimacy.
Always Use 2FA: By requiring a second form of verification, 2FA makes it significantly harder for unauthorized users to access your accounts, even if they have your password.
Be Skeptical: If something feels off, trust your instincts and investigate further.
Conclusion
As we dive into the holiday season, let’s stay informed and cautious. Scammers are becoming increasingly sophisticated, and it’s up to us to protect ourselves and others. Share this post to raise awareness and help prevent others from falling victim to these scams.
I have been tracking this and similar campaigns targeting Hong Kong, Dubai and Malaysia. The increased sophistication of these operations is a continuing trend. Seeing an operation involving pictures of my own advertised items hosted on malicious infrastructure to be used in phishing was truly surprising. Individuals and organisations must practice continued vigilance especially around seasonal holidays.
I was very pleasantly surprised to find that Carousell identified and removed the malicious actor from their platform on the same day I encountered and researched this campaign.
Stay safe and happy holidays!
Medium Post: https://medium.com/@binhashm/my-close-call-with-a-carousell-smishing-scam-this-christmas-39639b4988da
P.S:
If you are in HK and interested in a well used JUTHOLMEN IKEA sofa please get in touch!!

